Research Data Management and Publishing
Data Storage and Information Security
This topic is about data storage, the making of backups and information security in the course of a research project.
Data can be stored by using different ways and methods, such as cloud solutions, hard drive, external hard drive, or mobile devices.
All participants of a research group have to be clear about which data storage methods are acceptable.
The objective of these activities is to ensure:
- Availability – data must be available and accessible
- Integrity – data must be accurate, complete and up-to-date
- Confidentiality – data must be available only for authorised persons or systems
The most secure option is, certainly, to use the central servers of the university, which are provided with IT services, including the making of backups.
Using of cloud services is also secure, but it can have shortcomings, especially in the cases where personal data are processed. Providers of cloud services (e.g. Dropbox, OneDrive) may not be located in the European Union and it cannot be guaranteed that the data would always be processed according to the General Data Protection Regulation. That means, these services are not acceptable in storing research data.
Unencrypted personal data must not be stored in remote servers (‘in the cloud’).
Cloud solutions are well suitable for the cooperation of researches in different locations.
Data are often stored in the computers which are used by the research group or in personal computers of the work group members. In such cases, the making of backups may become a problem.
Making of a backup is the creation of a copy of the state of the data or the programmes at a given moment, which would allow to restore them up to that given moment after a security incident.
The incident is some unfortunate event, due to which data are lost, such as the physical destruction due a fire, unintentional deleting, a crash of the hard drive or the operating system, etc.
Making of backups should follow the 3-2-1 rule, meaning that three copies of the backup should be stored on two different storage media, one of which is located far away at a different location.
Each researcher is responsible for using the most secure data storage environment or device. It is quite difficult to follow this rule when using external hard drives or mobile devices. Therefore, when the gathering of data requires the using of some mobile device (tablet, camcorder, audio recorder), it is advisable to save the data at the earliest possible moment on some secure media. Mobile devices are also prone to malfunctioning, destruction, loss or theft, making them less secure.
This example gives an idea about how and where master’s students store their data. We can conclude that even with data-intensive research, if 81% of the data are on personal computers or external hard drives, it is not stored in the most practical and safest way
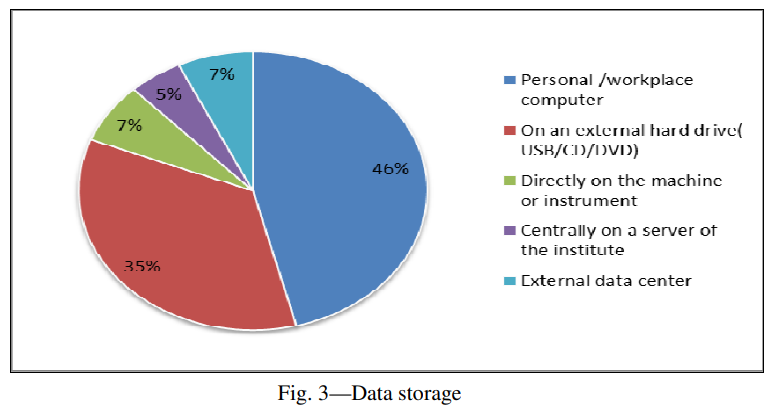
Meera B.M., Hiremath V. Data-intensive research in physics: challenges and perspectives. Ann Lib Inf Stud 65 (2018) 43-49.
Compared to postgraduate practices in 2018, the data storage locations used by researchers were somewhat more secure in 2022, but there was still too much use of local and personal devices:
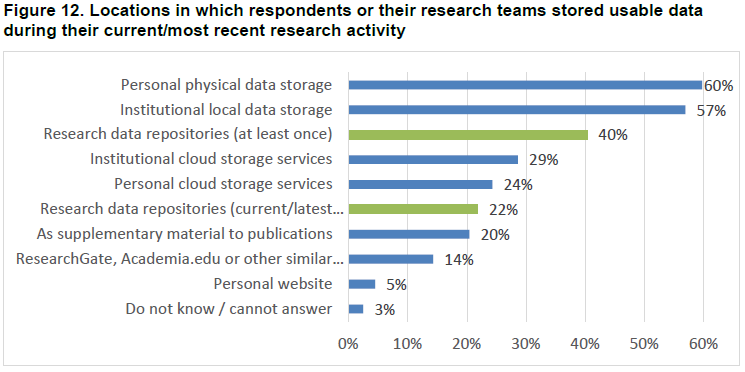
Resource: European Commission, Directorate-General for Research and Innovation, European Research Data Landscape – Final report, Publications Office of the European Union, 2022, https://data.europa.eu/doi/10.2777/3648
Data management plans should specify where the data are stored, who should make backups and how often the backups should be made, and for how long a period these backup copies should be stored.
Another important factor includes organisational and physical security, such as the training of new staff members, possible problems with staff members who leave the group, internal rules of the workplace, fire safety, locking of doors, etc.
In case of data-intensive research, it would be advisable to carry out a risk analysis in the work group and to answer the questions, what should be done if …
- the IT systems malfunction
- there are blackouts, deluges, fires
- someone’s computer or mobile device is lost or stolen
- malware is discovered in some devices
- a member of the work group leaves or dies
- etc.
Risks should be assessed (the probability of their occurrence and possible damage) and it should be decided which risks can be prevented, and when it is necessary to manage the consequences.
Data storage and backup options in University of Tartu.


